- +65 6397 5396 / 6397 5523
- sales@vgctechnology.com
SMBs – Here’s Why You Need Microsoft Defender for Business

- February 10, 2023
- 4:13 am
It’s a myth that smaller organizations are not targeted and attacked. Security is still one of the most pressing concerns and most difficult responsibilities that businesses face today. With an increase in cyberattacks on small and medium-sized businesses, threats are becoming more automated and indiscriminate, striking at a much higher rate. We’ve seen a 300% increase in ransomware attacks in the last year, with more than half of them targeting small businesses. To address this, Microsoft is investing in security solutions that are specifically designed to aid in their protection.

Extortion and disruption from ransomware are today’s top security threats. Your company requires increased protection from these and other threats at an affordable price, so having Microsoft Defender for Business will give you peace of mind.
What is Microsoft Defender for Business?
Microsoft Defender for Business was included as part of Microsoft 365 Business Premium, and Standalone solution in preview. it is an endpoint security solution for small and medium-sized businesses (SMBs) with up to 300 users. The service offers attack surface reduction, threat management, anti-malware protections, as well as automatic investigation and remediation features.
Microsoft Defender for Business is more than just an antimalware solution for client devices. It does provide such protection across client devices, including those running Android, iOS, macOS, and Windows.

What are the features of Microsoft Defender for Business?
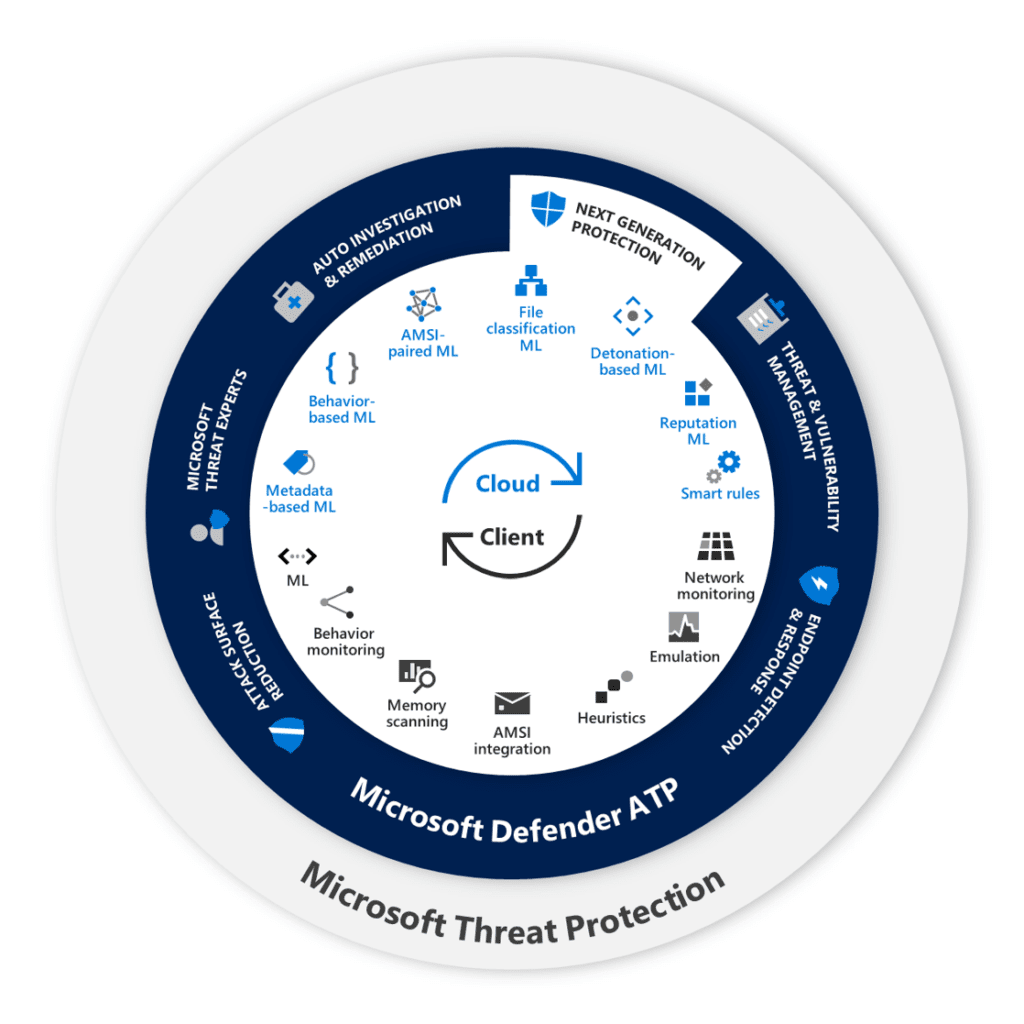
In addition to antimalware protection, Microsoft Defender for Business can Identify, Protect, Detect, and Respond for small and medium-sized businesses:
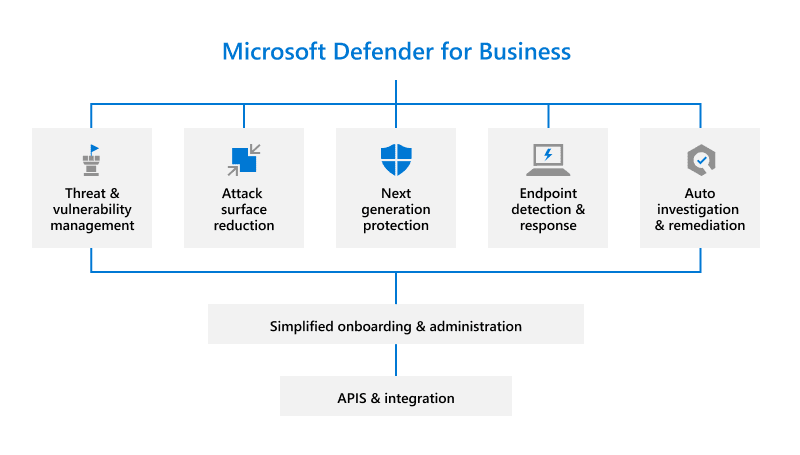
- Threat and vulnerability management
- Attack surface reduction
- Next-generation protection
- Endpoint detection and response, and
- Automated investigation and remediation capabilities.
Identify
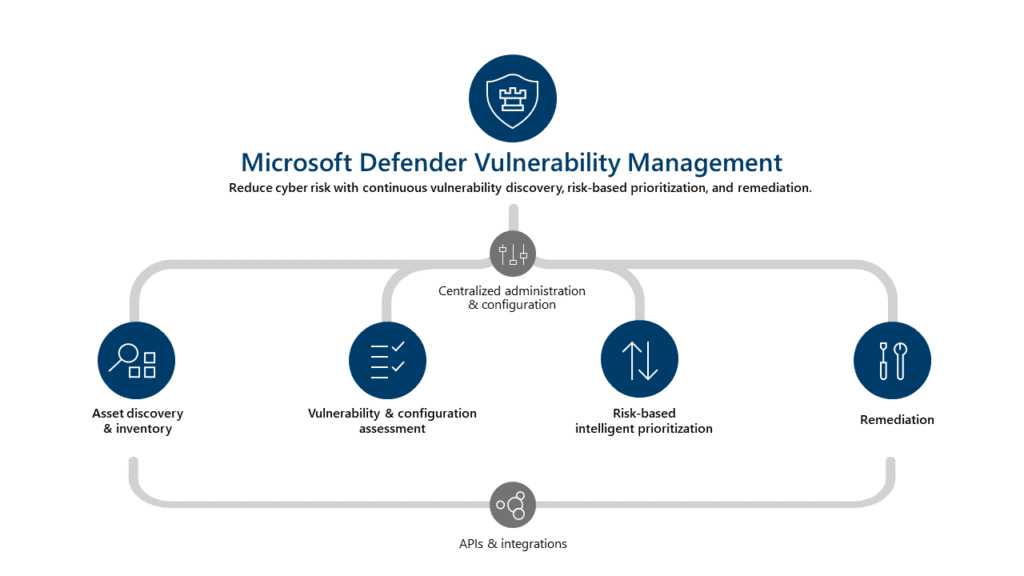
Threat and vulnerability management helps you to prioritize and focus on the weaknesses that pose the most urgent and highest risk to your business. By discovering, prioritizing, and remediating software vulnerabilities and misconfigurations, you can proactively build a secure foundation for your environment.
A proactive approach to endpoint security known as “threat and vulnerability management” informs your company about vulnerabilities and the security of your configuration posture. These insights enable you to plug security holes before they result in a breach.
You cannot secure what you cannot see. You can’t rely on a VPN connection to scan endpoints because remote users are constantly entering and exiting your network. Instead, this capability is added to ensure continuous visibility of remote endpoints across your global hybrid IT infrastructure. Everything from threat and vulnerability scanning to corrective action deployment is seamless.
Protect
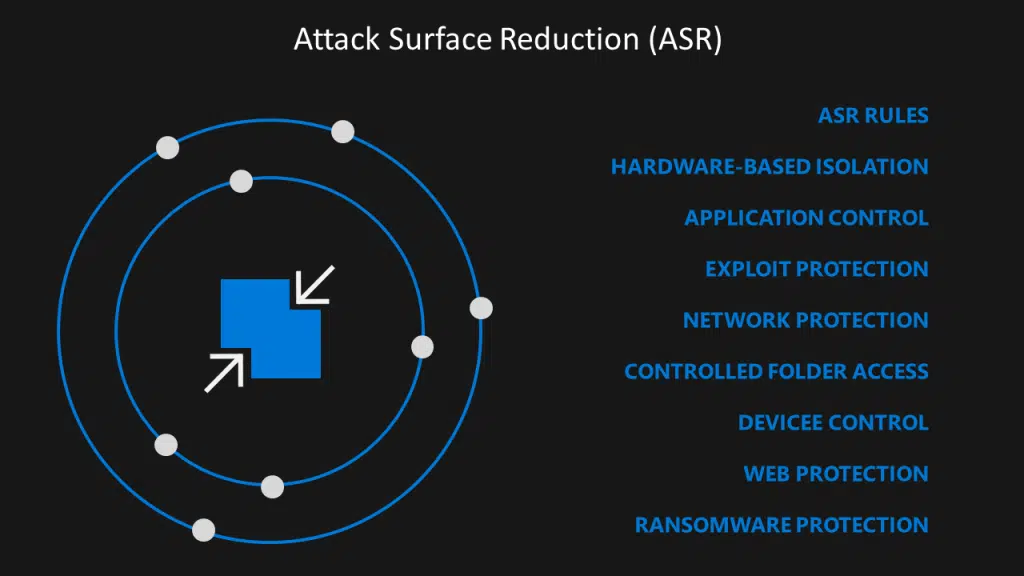
Options help to minimize your attack surface (like the places where your company is vulnerable to cyberattacks across your devices and applications), leaving bad actors with fewer ways to perform attacks.
Limit the opportunities for attackers to target your application. This concept is known as attack surface reduction. Resources not exposed to the Internet are less vulnerable to attack, limiting an attacker’s ability to attack application availability.
For example, if you do not expect users to interact directly with certain resources, make sure that those resources are not accessible over the Internet. Similarly, do not accept traffic from users or external applications on ports or protocols that are not required for communication.
Next-generation protection
Helps to prevent and protect against threats at your front door with antimalware and antivirus protection—on your devices and in the cloud.
The modern method of detecting zero-day threats is to use AI and Deep Learning to analyze executables and file-less threats prior to execution, during execution, and the ability to roll back an attacker’s actions. With nearly 1 million new threats being created every day, traditional signature-based antivirus can’t keep up, and by the time they do, it’s too late. The simple story is that advanced Next-Generation Endpoint Protection and Response is simply effective and has been proven time and time again.
In today’s world, where almost every business faces a breach at some point, the bad guys use tools that are as good as or better than the good guys. Every business, large or small, requires a layered security approach. With the increase of silent attacks hiding in encrypted tunnels and traveling undetected throughout your network, it is critical that you protect all of your endpoints to avoid any weak entry.
Detect and respond
Endpoint detection and response
Provides behavioral-based detection and response alerts so you can identify persistent threats and remove them from your environment.
Endpoint detection and response (EDR), also known as endpoint threat detection and response (ETDR), is a unified endpoint security solution that combines real-time continuous monitoring and endpoint data collection with rules-based automated response and analysis capabilities. Anton Chuvakin of Gartner proposed the term to describe emerging security systems that detect and investigate suspicious activity on hosts and endpoints, using a high level of automation to enable security teams to quickly identify and respond to threats.
An EDR security system’s primary functions are to:
- Monitor and collect activity data from endpoints that could indicate a threat
- Analyze this data to identify threat patterns
- Automatically respond to identified threats to remove or contain them, and notify security personnel
- Forensics and analysis tools to research identified threats and search for suspicious activities
Automated investigation and remediation capabilities
Help to scale your security operations by examining alerts and taking immediate action to resolve attacks for you. By reducing alert volume and remediating threats, Defender for Business allows you to prioritize tasks and focus on more sophisticated threats.
Microsoft Defender for Endpoint’s automated investigation and remediation (AIR) capabilities can assist security operations teams in responding to threats more efficiently and effectively. When suspicious activity is detected on a machine, Microsoft Defender for Endpoint initiates an automated investigation.
This investigation begins with an examination of the malicious entities that triggered the investigation and then moves on to the collection and examination of other items associated with it. During the investigation, files, processes, services, register keys, and other areas that may contain threat-related evidence are inspected. The scan produces a list of entities associated with the alert, as well as a verdict (malicious, suspicious, or clean).
How to get Microsoft Defender for Business
- Try or buy the standalone version of Defender for Business.
- Get Microsoft 365 Business Premium, which includes Defender for Business.
- Work with a Microsoft partner who can help you get everything set up and configured like VGC Technology, as a Microsoft Solutions Partner for SMB, we are very experienced in providing solutions that are effective and affordable.

Small-to-medium organizations subscribing to Microsoft Defender for Business get Microsoft’s security operation team’s support. It’s a perk for smaller organizations, which may have just one IT person doing everything.
Lefferts added that Microsoft Defender for Business automatically investigates possible security incidents on a “24×7” basis, and users get a dashboard view. IT pros get the ability to isolate and lock potentially compromised devices using the service.
What's new in Microsoft 365 Business Premium and Microsoft Defender for Business
Applies to:
January 2023
- Attack surface reduction capabilities are rolling out. Attack surface reduction capabilities in Defender for Business include attack surface reduction rules and a new attack surface reduction rules report. Attack surface reduction rules target certain behaviors that are considered risky because they are commonly abused by attackers through malware. In the Microsoft 365 Defender portal (https://security.microsoft.com/), you can now view a report showing detections and configuration information for attack surface reduction rules. In the navigation pane, choose Reports, and under Endpoints, choose Attack surface reduction rules.
- Default experience for Defender for Business when an enterprise plan is added. Defender for Business now retains its default experience (simplified configuration and setup) even if an enterprise plan, such as Defender for Endpoint Plan 2 or Microsoft Defender for Servers Plan 1 or 2 is added. To learn more, see What happens if I have a mix of Microsoft endpoint security subscriptions?
Share This:
Popular Post
Connect with us
Related Posts

SMBs – Here’s Why You Need Microsoft Defender for Business
It’s a myth that smaller organizations are not targeted and attacked. Security is still one of the most pressing concerns and most difficult responsibilities that
Corporate Headquarters
+65 6397 5396
+65 6397 5523
- 1 Gateway Drive,
- #17-10 Westgate Tower
- Singapore 608531
Send Us a Message
Need to get in touch with us? Our team is fresh and always open to business. If you can’t find the answer you’re looking for, we are here to lend a hand.