
- +65 6397 5396 / 6397 5523
- sales@vgctechnology.com
Cybersecurity health and how to stay ahead of attackers with Linda Grasso

- February 20, 2023
- 5:44 am
A version of this article was first published on the Microsoft blog.
Brooke Lynn Weenig - Senior Product Marketing Manager
Linda Grasso - Founder and Chief Executive Officer, DeltalogiX
The security community is continuously changing, growing, and learning from each other to better position the world against cyberthreats. In the latest post of our Community Voices blog series, Microsoft Security Senior Product Marketing Manager Brooke Lynn Weenig talks with Linda Grasso, the founder and chief executive officer of DeltalogiX, a blog that provides business leaders with the latest technology news. The thoughts below reflect Linda’s views, not the views of Linda’s employer or Microsoft, and are not legal advice. In this blog post, Linda talks about security trends, identity and access management, and the human and technology connection.
Brooke: What are today’s biggest data security challenges?
Linda: Nowadays, all businesses, whether large or small, handle a huge amount of data, and protecting it is critical to avoid damages related to its theft. The collection of data is essential because it optimizes processes, makes production more efficient, and reduces costs.
Connecting it to the cloud and being able to find information anywhere is a great opportunity, but we should never forget to protect our backs. How? Through the implementation of proactive and reactive cybersecurity strategies. With a cyber emergency response plan, we can draw up a guide highlighting the actions to be taken in the event of a cyberattack. A successful, growth-oriented business will necessarily pursue a journey toward digital transformation and encourage the connection of devices and people. At the same time, however, it’s imperative to monitor the security of information systems.
Brooke: How is internal threat protection a key component of a well-thought-out data security strategy?
Linda: When we talk about cybersecurity, we often think about how to protect the company from external threats. But sometimes those threats come from within company walls. Employees who pose a threat may not be caught until the damage is so severe as to be evident because they know how to move within the network. Or the people who allowed an intrusion may not even be aware of what they did.
How to thwart the insider threat? First, invest in training to make sure all employees know the risks of sharing information online. It is critical to educate employees on how to handle data. Second, establish roles and permissions for accessing confidential data and documents. By adopting identity and access management logic, for instance, employees will have specific permissions to access the information they need to do their jobs.
Again, we should never underestimate the importance of having security systems that identify threats and predict possible attacks. In conclusion, always be on the lookout for alerts generated by platforms and suspicious movements. These include much higher bandwidth consumption at unusual times or data passing from someone who does not have the permission to do so.
Brooke: We are focused on creating a human-first and tech-driven approach to security. What does it mean to you to strike a balance between these two elements?
Linda: Bringing the potential of the human mind back into machines is a challenge that has experts and scientists around the world engaged. The business context is one of people and technology. This balanced combo can recreate the potential of the two mental hemispheres: the left hemisphere, which is the seat of rationality and logical, mathematical thinking, and the right hemisphere, the seat of imagination and creativity. The two hemispheres of the human brain are interconnected.
In the same way, an innovative company will have to connect the creative potential stored in the minds of people and the analytical and rational potential programmed into the software. Creativity is as important as rationality and must be trained in business contexts, where stagnation is the greatest obstacle to growth and ally of security breaches.
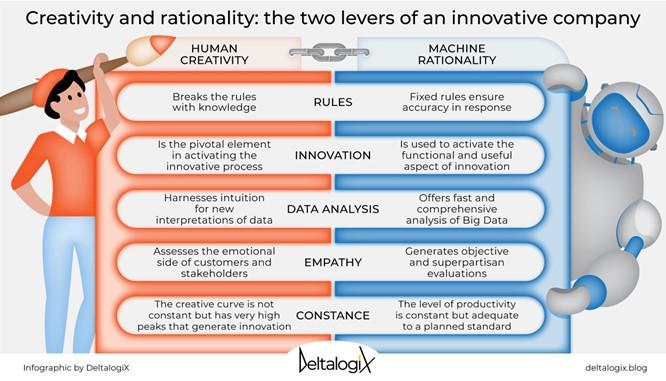
Figure 1. Creativity and rationality are the two levers of an innovative company. The qualities pertaining to the Human Creativity Lever include: breaks the rules with knowledge; innovation is the pivotal element in activating the innovative process; data analysis harnesses intuition for new interpretations of data; empathy assesses the emotional side of customers and stakeholders; and the creative curve is not constant but has very high peaks that generate innovation. The qualities pertaining to Machine Rationality include: fixed rules ensure accuracy and response; innovation is used to activate the functional and useful aspect of innovation; data analysis offers fast and comprehensive analysis of Big Data; empathy generates objective and superpartisan evaluations; and the level of productivity is constant but adequate to a planned standard.
Brooke: More than 80 percent of organizations are multicloud. How important is creating solutions that span clouds, platforms, devices, and apps?
Linda: Surrounded by a fast-paced, changing world, companies choose to define their own strategy and create software applications in-house. What is needed is a cloud that lets an IT team configure, run, and enhance responsive applications in modern, dynamic environments. That is why organizations end up turning to multiple clouds simultaneously.
One of the most important benefits is security. The multicloud architecture requires a “command platform,” like a cloud management system. Through this, it is possible to manage access, know at any time the structure of the cloud, and know and manage data storage. Also, thanks to communication between platforms, it is possible to make processes more efficient, reducing bottlenecks and slowdowns.
Finally, interoperability enables learning how to operate in multiple clouds and the internal generation of those talents and skills that are hard to find externally: transversal skills and critical observation. It is increasingly vital to have a well-defined strategy for storing digital data.
Brooke: How have data security market trends adjusted in response to worsening macroeconomic conditions?
Linda: Almost daily, our global news cycle runs stories about cyberattacks on our systems. Whether it’s stealing data or seeking ransom, these reprehensible acts make us feel, at best, insecure, and perhaps even hostage to hackers. Of course, they also carry a significant cost to the companies that must reclaim their data, restore public trust, and pay the penalty for violating privacy and protection laws. How do we protect ourselves? To mitigate consequences, we train employees to recognize the scale of the problem so that they can identify early warning signs, just as we invest heavily in technological resources to monitor, prevent, and block nefarious users.
Globally, large technology players are innovating systems to make them less vulnerable to attack. For instance, the Zero Trust security model requires users—
Brooke: How does the industry view data protection within the context of cybersecurity?
Linda: How much data do employees have to deal with every day in the company? A lot, especially when we look at companies going digital. Despite the increase in cyberattacks in recent years, few companies still commit to in-house cybersecurity investments. Digital exposes our data to significant risk, and chief information security officers should raise awareness among leaders on this issue, where prevention is better than cure.
The benefits to the company in terms of economic and business impact are evident, so it is important to act from the first presentation of a cybersecurity solution. Indeed, losing customer data and stopping production or operations because of a systems attack carry significant image and economic costs, and few companies are willing to take these risks. If they do, it is because they are unaware or because they do not understand the entire process.
Brooke: What advice would you give to companies about where to start?
Linda: Cybersecurity is not something to be evaluated on a one-time basis or reserved for high-risk business areas. Today, with digitalization and data-centricity, we need a real, continuously updated cybersecurity strategy. We need initial planning and constant monitoring to make sure we are properly defending our business value. Having highlighted the experts and data to be protected, it will be necessary to plan activities and tools that allow people to make as few mistakes as possible.
First, activate backup systems that periodically and automatically save data from specific areas defined as sensitive or high-risk. Also, strategically, a recovery plan will need to be in place in case of damage to systems (disaster recovery). We can predict threats and plan preventive actions, but we will never achieve 100 percent risk coverage. When we manage services, the interruption of those activities would harm us and our customers, so it is essential to provide an alternative plan that ensures continuity of service while fighting cyberthreats, such as attacks aimed at preventing access to a system, like distributed denial of service (DDoS).
At this point in the strategy, remember to constantly update the entire information security system. Do not let your guard down when the implementation has been done correctly, people have been trained, you have learned cybersecurity procedures, and the security system proceeds automatically. Instead, it is as important, if not more important than the previous activities, to constantly update software and related procedures related to cybersecurity. Threats evolve rapidly and outdated systems may not do their job properly.
Share This:
Popular Post
Connect with us
Corporate Headquarters
+65 6397 5396
+65 6397 5523
- 1 Gateway Drive,
- #17-10 Westgate Tower
- Singapore 608531
Send Us a Message
Need to get in touch with us? Our team is fresh and always open to business. If you can’t find the answer you’re looking for, we are here to lend a hand.


